Use Tor. Use Empire.
Recently I used Empire at work on a phishing engagement because it supports macOS, Linux, and Windows hosts from one listener. You should try it out if you find yourself where you need Command and Control (C2) that is easy to use with many features.*
But that is not the topic of this post.
Many security experts say: "Use Tor. Use Signal." And I can agree on that to some extent. However, ordering food over Tor is difficult when the waiter is looking at you in the face. I guess context is everything. ¯\_(ツ)_/¯
I say "Use Tor. Use Empire." /snark
It's not difficult and using Empire through a hidden service solves some problems:
• You don't need a server on the Internet - put the C2 in a docker host locally or put it behind portal
• Keep your C2 anonymous - only the Empire Listener is exposed
• Doesn't require Tor to be installed on the host/target (tor2web)
• Secure by default (more on this)
On the downside:
• My Demo uses tor2web URLs - pretty easy to filter for a defender
• Not using tor2web type redirectors requires Tor to be installed on the host and then proxied via the tor socks listener via netcat (Mac/*nix) - on windows it's a bit more difficult (netsh and bypass-filter all the things)
• There have been attacks to de-anonymize tor hidden services (certain conditions apply).
Here's how to do it:
• Install Tor on your server where you will be using Empire.
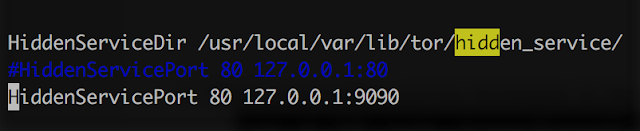
• Update the torrc to support the hidden service with the following syntax: HiddenServicePort 80 127.0.01:<listener port>
• Set up your listener. In the screenshot below I'm using .onion.to as the domain. It's typed correctly: https://y4hgaofmhx3bcml4.onion.to/:9090 Note the /:<PORT> after the onion.to -that's the correct syntax. I set the DefaultDelay and Jitter at higher intervals because Tor can be slow at times.
• After deployment, you should see this shortly:
Notice in the config that I didn't use a cert to force HTTPS agent communications. A couple reasons:
• The Tor2Web site in this demo uses TLS 1.2 AES-256-GCM with ECDHE_RSA for key exchange.
• Traffic from the Tor2Web URL redirector is encrypted via the normal tor encryption method all the way to the hidden service.
• Using a cert to force https in my testing resulted in failure. ಠ_ಠ
Ok that's it, enjoy your shells responsibly!
* Metasploit would have worked also, just wanted to give Empire a shot.





Hi, I really like this Blog. The problem is when I type "info onion" , it says
ReplyDelete"Invalid listener name"
Please guide me through this problem.
"It is not a mistake to commit a mistake, for no one commits a mistake knowing it to be one. But it is a mistake not to correct the mistake after knowing it to be one. If you are afraid of committing a mistake, you are afraid of doing anything at all. You will correct your mistakes whenever you find them." - Mohandas K. Gandhi
Delete