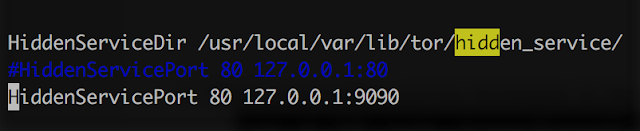
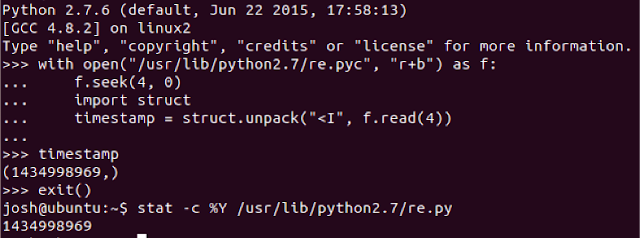
In News Archive
Tor Russia MITM Malware Injection: http://threatpost.com/researcher-finds-tor-exit-node-adding-malware-to-binaries/109008 http://www.theregister.co.uk/2014/10/27/tor_exit_node_mashes_malware_into_downloads/ http://www.infoworld.com/article/2839135/security/tor-project-flags-russian-exit-node-server-delivering-malware.html http://www.zdnet.com/rogue-tor-node-wraps-executables-with-malware-7000035060/ http://www.itworld.com/article/2838975/tor-project-flags-russian-exit-node-server-for-delivering-malware.html http://www.net-security.org/malware_news.php?id=2897 http://www.scmagazineuk.com/rogue-tor-exit-node-injects-malware-into-downloaded-binaries/article/379404/ http://www.scmagazine.com/tor-exit-node-found-to-add-malware-to-downloaded-binaries/article/379526/ http://www.theguardian.com/technology/2014/oct/28/tor-users-advised-check-computers-malware http://www.darkreading.com/attacks-breaches/researcher-shows-why-tor-anonymity-is-no-guarantee-of-security/d/d-id/1...