Posts
Showing posts from 2015
Add PE Code Signing to Backdoor Factory (BDF)
- Get link
- X
- Other Apps
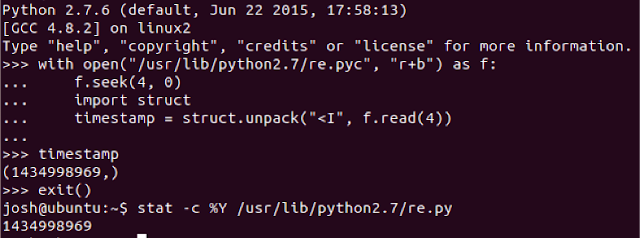
Backdooring Python via PYC ( /ˈpiː/ - /ˈwaɪ/ - /ˈsiː/)
- Get link
- X
- Other Apps
Yet Another Reason for HTTPS Everywhere: Internet Node Based Malware Command and Control Channels
- Get link
- X
- Other Apps
New BDF Feature: Import Table 'Patching'
- Get link
- X
- Other Apps